When we talk about data breaches, it’s common to only refer to the “records” that were exposed. The problem with this is that without factoring in the cost of data breaches, we lack context. After all, there are few clearer illustrations of business impact than how much it dents the bottom line.
In this article we’ll look at:
- Why data breaches happen.
- Main factors that drive data breach costs.
- Average cost of a data breach.
- Examples of data breaches in 2020 and 2021.
- How much these data breaches might have cost.
- What your organisation can do to mitigate the impact.
(If you’re short on time there’s a tl;dr summary at the end of the article)
Why Do Data Breaches Happen?
We have three main categories of data breach causes: human error, malicious attack, and system glitches.
But, thanks to an IBM Security report on the costs of data breaches, we can see that rarely is the techy side of things entirely to blame. No, 75% of the time, it’s the fleshy bit using the technology that’s at fault. Either through human error, or some form of malicious attacks.
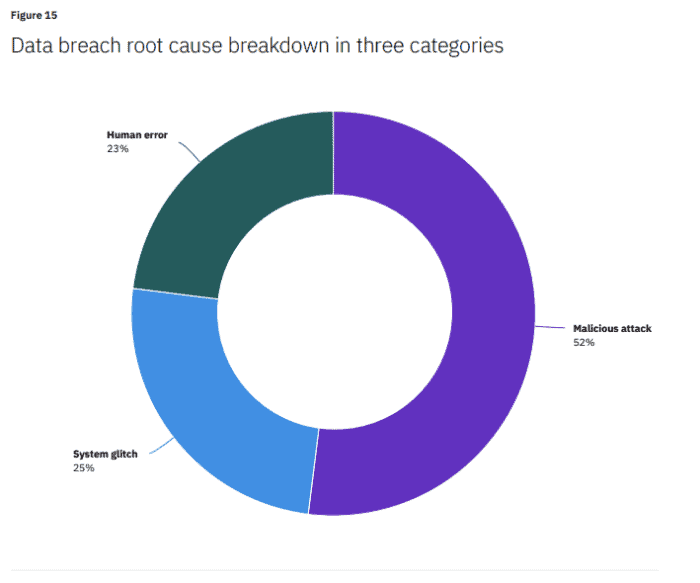
Source: Cost of Data Breach Report 2020, IBM Security
Looking at the malicious attack category a bit closer, we can see that dodgy cloud configurations and weak passwords can take a good chunk of the blame. Both of which can actually be mitigated with regular security awareness training and an effective security policy.
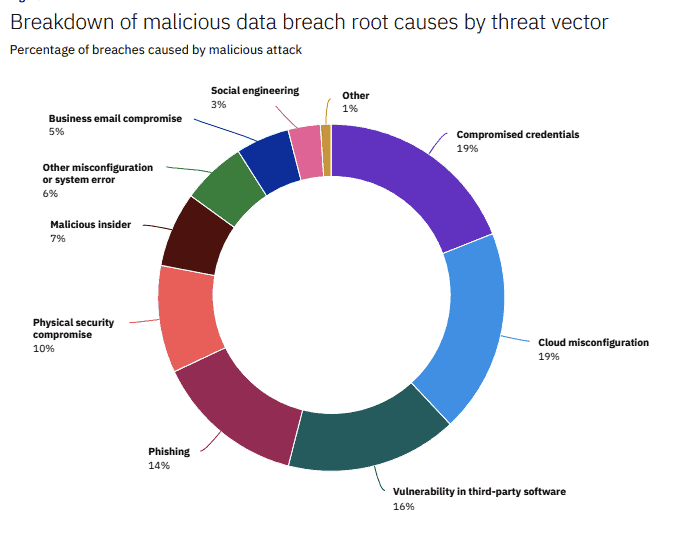
Source: Cost of Data Breach Report 2020, IBM Security
The complexity of modern security systems has no doubt led to the increased challenges faced by security teams. As different parts of the organisation need to tap into more external software, that opens up another threat vector to protect against. It’s also hard to ignore phishing attacks as a potential threat vector, as they account for 14% of malicious data breaches.
Calculating the Cost of Data Breaches
There are many factors to consider if we want to try and work out how much a data breach is likely to cost, but fundamentally we can break it down into four key cost centers:
- Detection and escalation: that’s anything a company does to detect a breach, like auditing services, for example.
- Notification: once an organisation has figured out there’s a problem, they need to communicate with not only their data subjects, but also regulators, legal experts, and regulatory consultants.
- Lost business: depending on the nature of the breach, an organisation can experience downtime which hits revenue, then longer term they’ll have to deal with brand damage.
- Ex-post response: after the breach has happened, and impacted users have been notified comes the influx of queries, potential legal costs, fines, and maybe offers and discounts to restore a bit of that tarnished goodwill.
On top of those main cost centers, there are a few more factors we can take into account. For example, the cost per record varies by country and industry, with US healthcare records being the most costly.
Then there’s the type of data itself. Customer PII (personally identifiable information) is the costliest and by far the most compromised type of data. But across the board, we can see the average cost per record for small to large data breaches clocks in at an unnerving $146.
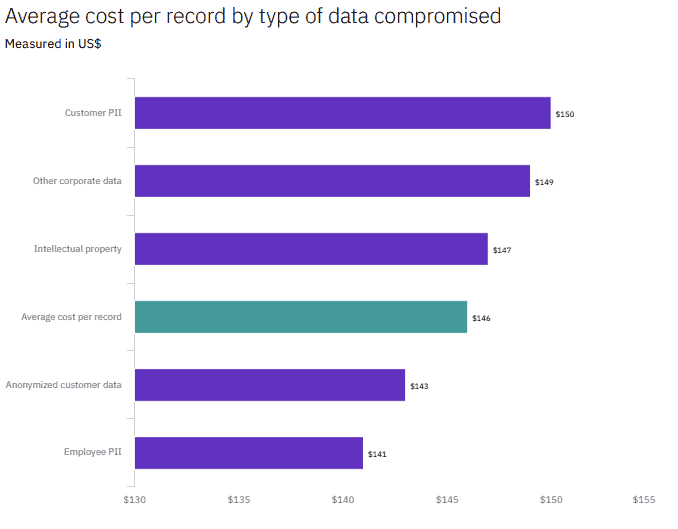
Source: Cost of Data Breach Report 2020, IBM Security
We say “small to large” because there’s another, scale-based cost factor:
The dreaded “mega breach”.
Any breach that involves more than 1 million records is defined as a mega breach; it represents an absolute worst case scenario for the organisations involved. These are also the breaches we hear about the most, simply because they are so big.
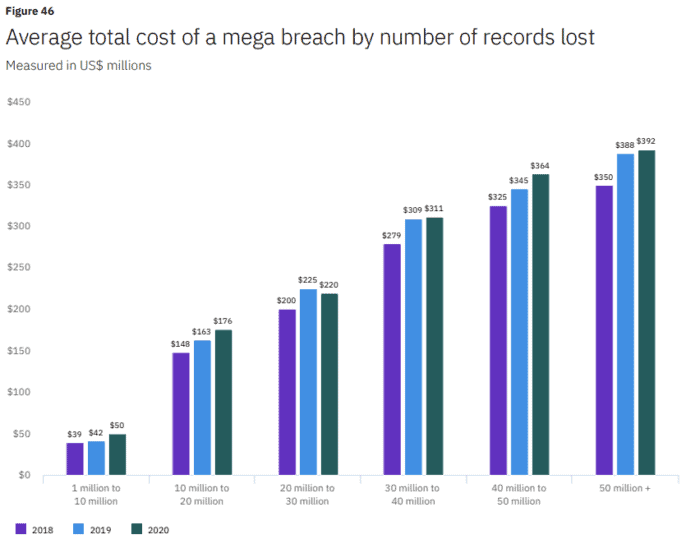
Source: Cost of Data Breach Report 2020, IBM Security
Being so vast, they also need to be analyzed separately from the small to large breaches, otherwise they’d end up skewing the numbers.
Recent Data Breaches and How Much They Cost
Based on the numbers above, we can estimate how much some of the more high profile data breaches have cost these companies.
In no particular order, here’s a look at some of the bigger data breaches we’ve seen over the last 12+ months or so, and how much they’ve cost.
533 Million – Facebook, April 03, 2021
Estimated cost: $3.7 billion
Type of data exposed: phone numbers, date of birth, locations (inc. historic data) full name, some email addresses.
In early April 2021, it emerged that the personal information of more than half a billion Facebook users had been leaked. Facebook declined to notify impacted users (perhaps as a cost saving exercise, as we know that notification and ex-post response are two of the main cost centers) after their data was scraped by exploiting a vulnerability in a now sunsetted feature.
250 Million – Microsoft, January 22, 2020
Estimated cost: $1.8 billion
Type of data exposed: email addresses, IP addresses, chat logs.
2020 was barely getting its boots on before Microsoft announced a major breach. While they didn’t cover figures, estimates peg the exposed record count at 250 million. Those records contained email and IP addresses, as well as chat logs between support staff and customers. Microsoft admitted this breach was the result of a “misconfiguration of an internal customer support database”.
9 Million – EasyJet, May 12, 2020
Estimated cost: $50 million
Type of data exposed: credit and debit cards
In May 2020, EasyJet announced 9 million customer records had been “accessed” in what they described as a “highly sophisticated cyber-attack”. This attack came at a bad time for EasyJet, as the pandemic’s impact was starting to take hold and involved credit card data. It also led to 10,000 people joining a lawsuit against EasyJet. Depending on the outcome of this case, the $50 million estimation may move into the billions, as each of the victims may be entitled to $2,500.
5.2 Million – Marriott, March 31, 2020
Estimated cost: $50 million
Type of data exposed: names, address, some phone and emails
The hotel leviathan, Marriott, revealed 5.2 million guests had had their data exposed after hackers obtained the login details of two employees. This was on top of an earlier breach in 2018 when one of Marriott’s subsidiaries was hacked, revealing millions of unencrypted passport numbers and credit card records.
What Can Your Organisation Do To Mitigate The Impact?
It’s evident that organisations of all shapes and sizes are not completely immune. Be it carelessness or malicious intent, when you have people interacting with machines, there are always going to be weak points.
You’ll also have people willing and able to exploit those weak points.
It’s not all doom and gloom, though because there’s plenty of things that your organisation can start doing right away to reduce the likelihood of a data breach.
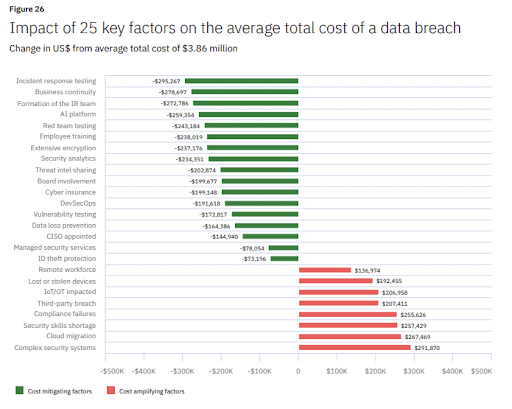
Source: Cost of Data Breach Report 2020, IBM Security
- Incident response testing: Knowing what to do when the worst happens can save your organisation over $230,000. Incident management tools help you pull all of the moving parts together, giving you an overview of the lifecycle of an incident when it happens. But it’s also vital that you put all of that to the test with simulated attacks. It’s not just the IT team who need to be involved in testing. Everyone from salespeople to support staff should be involved. Particularly with the constantly evolving nature of threats like phishing and ransomware. 96% of data breaches originate from email but running simulated phishing attacks to prepare your team and doesn’t have to be costly or time consuming.
- Security awareness training: The rise in remote working has added another layer of vulnerability, as employees use potentially insecure devices and connections to access sensitive data. So, now more than ever, employee cyber security training has the potential to reduce the risks (and potential costs) of data breaches.
- Extensive encryption: Many high profile data breaches have involved cases where sensitive data has been stored in unencrypted files, with passwords and credit card data sometimes just sitting there, unhashed, in plaintext. Rolling out company-wide encryption can have a massive impact, but it still relies on your employees being up to speed. Which leads nicely into the next solution.
- Policy management: If solutions like encryption are going to work, you need to have an effective cyber security policy in place and, even more importantly, make sure everyone knows what they’re supposed to be doing. Traditional approaches to policy management often involve HR having to chase down team members, sending increasingly irate emails asking if they’ve read and understood the new cyber security policy. And, if said team member has read it, can they please sign it and return it? Please? Instead, by deploying a cyber security policy management platform your organisation can spot gaps in staff knowledge, deficiencies in policy, and keep the costs of data breaches to a minimum.
TL;DR
- They can be cripplingly expensive: globally, data breaches cost organisations, on average, £2.8m per breach
- Most data breaches are malicious: more than half of all data breaches are the result of some sort of malicious activity.
- As Mum always said, “prior preparation and planning prevents poor performance”: Having an incident response team, testing your incident response plan, using encryption, and educating your users have some of the biggest impacts.