Password security has never been more important and Two Factor authentication has quickly become the go-to method to secure accounts. The humble password has been around for a long time and despite its popularity as the most common way to secure accounts, it no longer cuts it in an era of enhanced cyber attacks and data breaches.
In addition to this blasé approach to cyber security, hackers also have an impressive arsenal of tools that they can use to crack our password credentials. Social engineering remains the most popular method, but by using brute force attack, hackers have the power to test millions of possible password combinations every second.
It’s this vulnerability to attack that has fuelled the growth of finding alternative methods to secure online accounts, and two-factor authentication has quickly emerged as the go-to method to do this.
What Is Two-Factor Authentication?
Two-factor authentication, also known as 2FA, adds an extra layer of security to your online accounts. Rather than just confirming your identity with a simple username and password, you have to provide a second authenticating factor that only you can access. Really, it’s just another way to double-check that you are who you claim to be, thereby reducing the chance of someone fraudulently accessing your account.
How Does Two-Factor Authentication Work?
After logging into an account with a password, you will be prompted to confirm your identity by inputting a second form of identity verification.
There are three types of authentication methods that can be used to gain access:
- Something you know: A password, PIN, postcode or answer to a question (ex: mother’s maiden name)
- Something you have: A token, phone, credit card, SIM or physical security key
- Something you are: Biometric data such as a fingerprint, voice or facial recognition
Some of these verification methods are undoubtedly more secure than others but essentially it means that even if someone steals or guesses your password, they won’t be able to access your account without another authenticator.
If your account is protected by a second security factor, you may be given backup codes that can be used to disable two-factor authentication in the event you lose a physical security key, or an authenticator app on your mobile device.
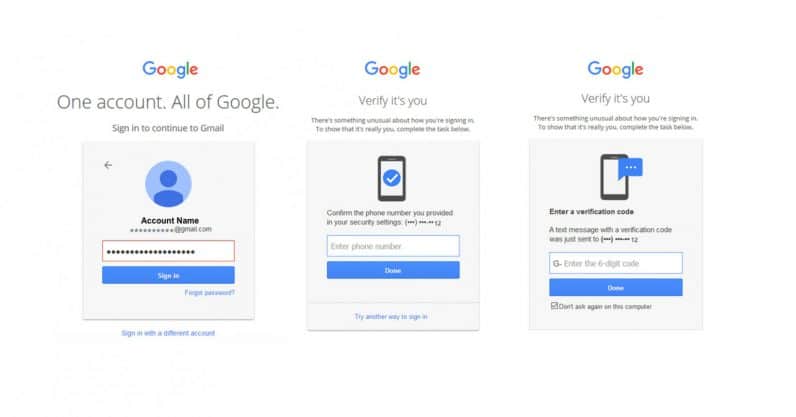
Image: Two-Factor Authentication Process Gmail
Benefits of Two-Factor Authentication
Two-factor authentication provides an extra layer of protection that can significantly reduce the chance of your accounts being hacked. As the number of security breaches continues to rise, it’s important to take the proper precautions to safeguard your data.
The benefits of using two-factor authentication include:
- Enhanced security – Two-factor authentication is a great way to reduce data theft and restrict unauthorised access to your account. The reality is that even if hackers know your password, unless they have your smartphone or another form of verification, they can’t access your device.
- Low cost – Most popular online services such as Google, Facebook, Microsoft and Amazon will provide two factor authentication for free. However, there may be some additional sites and services that will require a small fee for enhanced security options.
- Easy to enable – The great thing about two factor authentication is how easily it can be set it up on all your accounts. To enable two factor authentication, simply go into settings and turn it on. The next step is to sync your mobile phone to generate a one time code.
Why Organisations Need to Use Two-Factor Authentication
In recent years, there has been a significant increase in the number of businesses that are adopting two-factor authentication as a means of protecting sensitive company data. It provides an extra barrier that can make all the difference between an attempted hack and a business crippling data breach.
Many organisations are also now subject to compliance regulations that require them to implement two-factor authentication to keep certain types of information private and secure from interception. This could be for logging in, resetting a password or to provide a stronger authentication process for the protection of sensitive data like personally identifiable or financial information.
Aside from complying with regulatory standards, two-factor authentication can help improve flexibility and productivity in the workplace. With an increasing number of employees working remotely, two-factor authentication enables them to access company data without compromising corporate networks.
Is Two-Factor Authentication Secure?
There’s no doubt that two-factor authentication improves security and provides another layer of defence to the simple login process. However, as with many other forms of security, it can be vulnerable to attack. If a hacker is persistent enough or has the knowledge and experience to circumvent these measures, then they will.
Unfortunately, the human element continues to be the most exploitable weakness in the security chain. Using sophisticated social engineering techniques, hackers can attempt to intercept text messages, hack email accounts, and in a number of reported cases, they’ve even impersonated individuals to authorise a password reset over the phone.
That being said, these cases are rare. On the whole, multi-factor authentication is safe and provides an additional layer of security that can act as a deterrent to would-be attackers.
Enhance Your Cyber Security with Effective Employee Training
To strengthen your organisation’s cyber security, we recommend exploring these articles:
3 Ways to Add Personality to Your Security Awareness Programme
What Is a Cyber Security Policy? Importance and Best Practices Explained
Understanding Cyber Security Training Cost: What You Need to Know
Alternatively, request a free demo of our advanced Cyber Security Training for Employees to see how effective training can enhance your defense against cyber threats.
