The continual stream of high-profile data breaches has made us acutely aware of how valuable our data has become and the damage that can ensue if it falls into the wrong hands.
There are a host of reasons why hackers want to get their hands on our sensitive data but more often than not, it all comes down to money. Our data can be used to commit identity fraud, traded on hacker’s forums, or sold on to the highest bidder on the dark web.
The dark web provides the perfect platform for hackers to trade their stolen data without fear of reprisal. It can only be accessed using specialist software and any websites hosted on the dark web are encrypted and can’t be found using traditional search engines or browsers.
Most sites hide their identity using a Tor encryption tool. Tor effectively directs internet traffic through a series of proxy servers run by thousands of volunteers around the world. This makes it extremely difficult for anyone to identify the user, their location, or browsing habits.
The anonymity this provides makes it a huge draw to those users that want to engage in illicit or fraudulent activities such as drug trafficking, gun smuggling, prostitution, counterfeit goods, not to mention the massive market for stolen credentials and personal data.
A recent study from Digital Shadows has suggested that there are as many as 15 billion stolen credentials circulating on the dark web giving us an idea of the sheer scale of this market.
This vast underground criminal network operates 24 hours a day, 7 days a week and provides hackers with the ideal location to sell and profit from their stolen data.
But how much is our data actually worth?
Surprisingly, not as much as you think! There are several factors that will affect the price your data fetches online, but it all comes down to supply and demand. If there is a low supply of particularly valuable information, then this will obviously become more attractive to criminals.
There are also different prices placed on different types of data. One of the hottest commodities to buy in this underground network is stolen personally identifiable information (PII). This is data that can be used to identify or locate an individual and typically includes usernames, passwords, and contact details.
Personal Health Information (PHI) has also become increasingly valuable and can sell for anything between $100 and $350. This data can include dates of birth, names of relatives, medical procedures, test results, and in some cases financial information and criminal records.
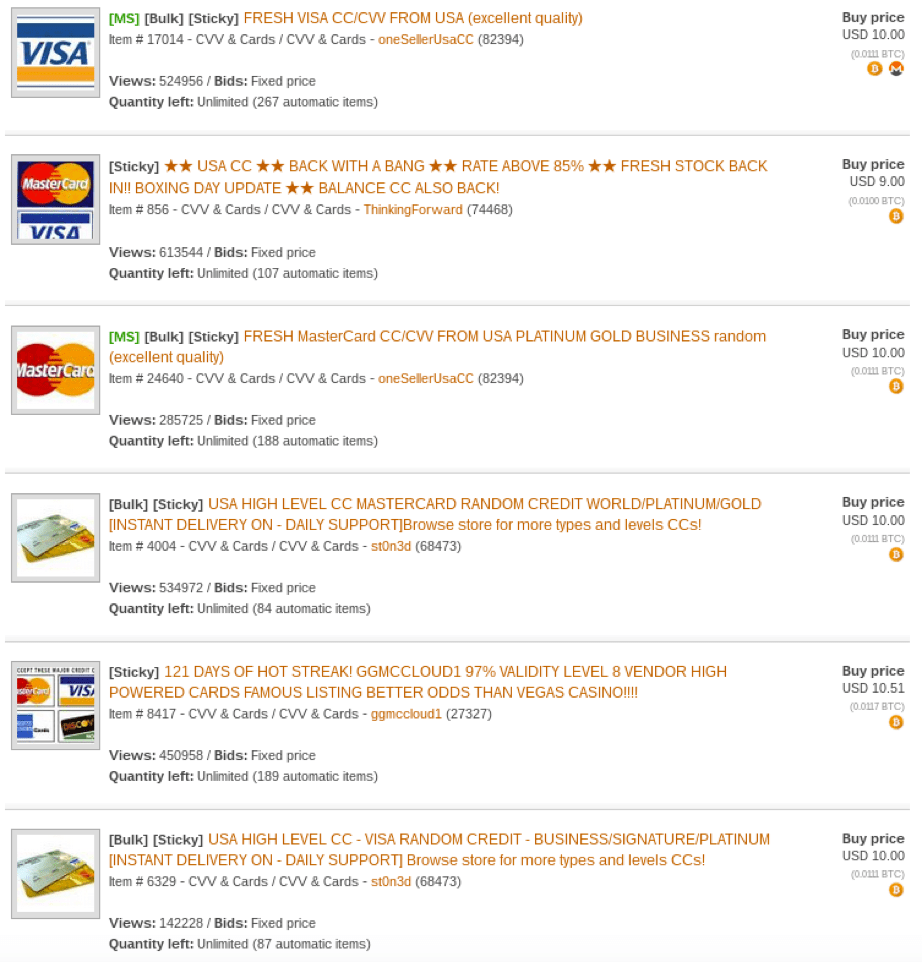
Credit card information is one of the most commonly trafficked data sets on the dark web and is sold for anything between £5 and £30 per card.
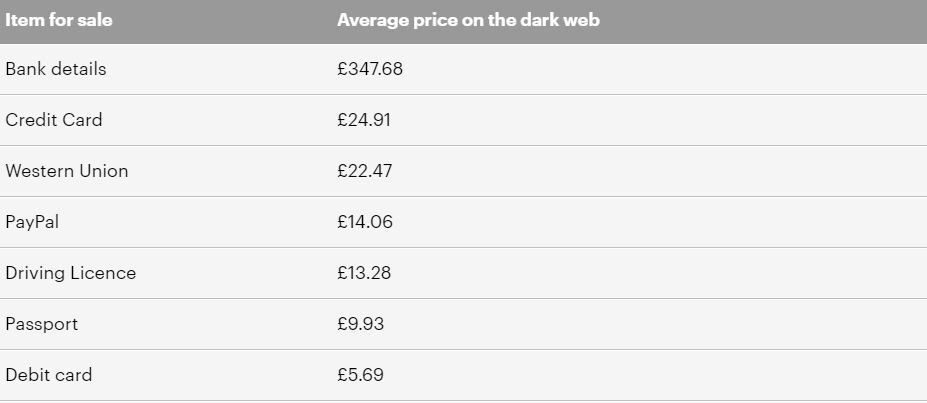
A recent report from Virtual Private Network (VPN) comparison service Top10VPN.com, found that social media login details can be bought for as little as £1, whereas one of the most sought after data sets includes hacked bank account details, which can be bought for roughly £347.
One of the main reasons our data is being traded at such low prices is because hackers can obtain it so easily. This is in part being fuelled by the huge increase in data breaches and the billions of confidential records that are exposed each year.
It’s interesting to note that after British Airways was breached in 2018, BA account details flooded the dark web and could be purchased for £31.94, a 375% price increase on the previous year.
It’s clearly a lucrative market and as long as this bustling underground network continues to thrive, cyber attacks will remain a constant threat to individuals and businesses throughout the world. Fortunately, there are a number of steps we can take to protect our data online:
How to Protect your Data online
- Create strong and unique passwords
A strong password should be between 10-15 characters long, a mix of uppercase and lowercase letters and include numbers or symbols. For extra security, a passphrase can be created which is a password composed of a sentence or combination of words. The first letter of each word will form the basis of your password and letters can be substituted with numbers and symbols to make it even more secure.
- Never click on suspicious links
Phishing scams are carefully crafted to trick you into entering confidential information such as an account number, password, or date of birth by clicking on a link. The message may also include an attachment that once opened will directly infect your computer with malware. Red flags often include a mismatched URL, poor spelling and grammar, requests for sensitive information, unexpected correspondence, or the use of threatening or urgent language.
- Be careful what you post online
To reduce your chance of being hacked, think more carefully about what you post online. Take advantage of enhanced privacy options, restrict access to anyone you don’t know, and create strong passwords for your social media accounts.
- Install anti-virus software
Anti-virus software detects threats on your computer and blocks unauthorised users from gaining access. Software should also be updated on a regular basis to prevent hackers from gaining access to your computer through vulnerabilities in older and outdated programs. Regular software updates will ensure that you have the most up to date versions released by the manufacturer, thereby reducing your chance of attack.
- Avoid using public Wi-Fi
Public Wi-Fi requires no authentication to establish a network connection, allowing direct access to unsecured devices on the same unencrypted network. A VPN can be used to encrypt your internet connection making it secure and protecting your privacy. Other safety measures include turning off sharing, sticking to secure sites, and switching off Wi-Fi when not in use.
