A new attack campaign phishes for users’ Gmail credentials and immediately leverages those details to steal access to victims’ accounts.
The attack begins when a user receives an email to their Gmail account. The email might come from someone whom the recipient might know but whose account the attackers have already compromised. As with most phishing campaigns, it comes with an attachment. Most of the attack emails appear to carry an attached image that is familiar to the recipient.
One would think clicking on the image would cause a preview to pop up. But that doesn’t happen. Mark Maunder, chief executive officer of WordFence, explains in a blog post:
“Instead, a new tab opens up and you are prompted by Gmail to sign in again. You glance at the location bar and you see accounts.google.com in there. It looks like this….”

The last thing a user wants to do is sign in using this convincing (but fake) Google login page. Doing so would provide the attackers with their Gmail login credentials. To make matters worse, if they do acquire their details, the attackers don’t waste any time in using them to compromise the user’s account and distribute phishing emails to some of their contacts.
As one commenter on Hacker News describes it:
“The attackers log in to your account immediately once they get the credentials, and they use one of your actual attachments, along with one of your actual subject lines, and send it to people in your contact list.”
“For example, they went into one student’s account, pulled an attachment with an athletic team practice schedule, generated the screenshot, and then paired that with a subject line that was tangentially related, and emailed it to the other members of the athletic team.”
To protect themselves against this attack campaign, users should first look at the location bar of a Google sign-in page a bit more closely before they log in. Google’s actual sign-in page should show nothing in the sign-bar before “accounts.google.com” except “https://”.
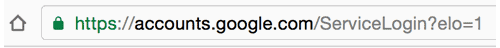
The scam’s use of “data:text/html” gives away the scam’s use of a file, that is, a fake Gmail login page.
Users should also enable two-step verification on their accounts. This feature will help protect users’ accounts even in the event someone does steal their username and passwords.
At the same time, organizations should help educate their employees about phishing scams. Simulated phishing campaigns oftentimes get the point across to users when it comes to looking out for suspicious emails. Organizations can design and send out these emails via the use of third-party security awareness training software.
Does this solution sound of interest to you?
If so, contact Metacompliance today and learn how its phishing simulations can help take your employees account security to the next level.



